The following article describes the required steps for setting up Single Sign-On (SSO) with Secure Network Communication (SNC) and Kerberos encryption.
Warning! SAP officially does not support the Kerberos Wrapper Library (gx64krb5.dll) anymore.
Warning! Single Sign-On availability
ABAP application server has to run on a Windows OS and SNC with Kerberos encryption setup on SAP.
Requirements #
- The SAP ABAP application server runs under a Windows operating system.
- The BI client (which calls the extraction) runs under Windows.
- The SAP Kerberos Wrapper Library (gsskrb5) is used as the SNC solution.
“Double Hop” Issue #
SNC solution must support the Windows credentials being passed on by an Xtract product.
Since Active Directory is based on Kerberos, a “Double Hop” issue may occur.
Here is a possible solution to the “Double Hop” issue:
For security reasons, Kerberos does not allow credentials to be passed on. But there are Kerberos extensions from Microsoft (S4U extensions) that allow credentials passing on. These extensions are also known as “constrained delegation”. Because the Kerberos Wrapper Library uses the Microsoft extensions for Kerberos to work around the “Double Hop” issue, it is only available for Windows. It therefore only works with SAP application servers under Windows and clients under Windows.
Unlike the Kerberos Wrapper Library (gsskrb5) from SAP (according to SAP), SAP’s Common Crypto Library does not explicitly support credentials to be passed on. The Kerberos Wrapper Library (gsskrb5) used by multiple customers of Theobald Software products.
When using an SNC solution from a third-party vendor, use either the Kerberos Wrapper Library or a corresponding solution of the third-party vendor.
Activation of HTTPS #
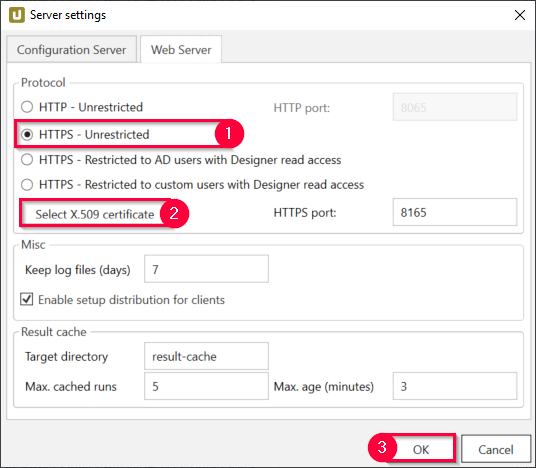
- Enable access control protocol HTTPS (1) within the tab Web Server settings.
- Reference an existing X.509 certificate (2).
- Click [OK] to confirm (3)
Note: Make sure to check the default ports depending on your product. HTTPS port 8165 is e.g., set up by default in Xtract Universal. BOARD Connector’s default HTTPS port 8197.
Configuration of Windows AD service account #
Using SSO with Kerberos SNC, the Xtract Universal service must run under a dedicated service account.
To do so, follow the steps as outlined in Running the Xtract Universal Service under a Windows Service Account.
Note: As of Xtract Universal version 5.0 SAP passwords are encrypted with a key that is derived from the Windows account that runs the XU service. The passwords can only be accessed from the same service account, when restoring a backup or moving the files to a different machine. If the service account changes, passwords need to be re-entered manually.
Server Settings #
Warning! Incompatible library
Xtract products run on 64bit OS only. Kerberos Wrapper Library gx64krb5.dll(64-Bit version) is required.
Download gx64krb5.dll from SAP Note 2115486.
- Copy the Kerberos Wrapper Library to the file system, e.g., to
C:\SNC\gx64krb5.dllof the machine, where the service is running. - Place the downloaded .dll file on each machine, where the Designer is running.
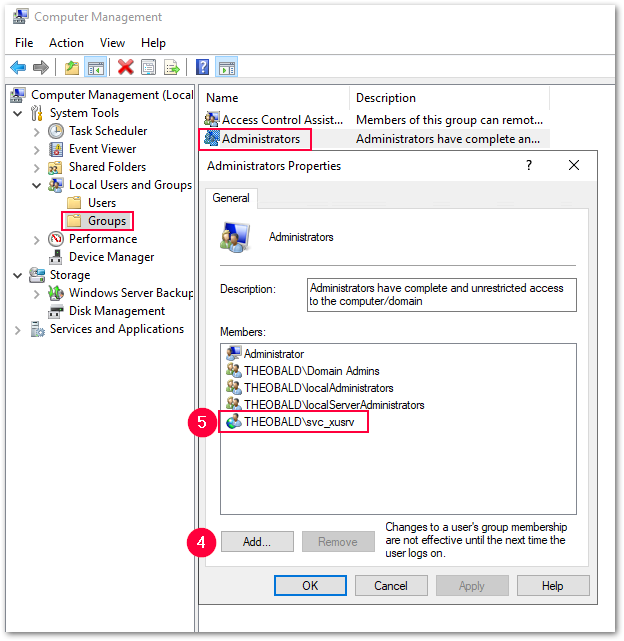
- Open “Computer Management” by entering the following command:
compmgmt.msc. - Under Local Users and Groups select Groups > Administrators.
- Click [Add] (4) to add the service account to the local admin group (5).
- Open “Local Security policy” by entering the following command:
secpol.msc.
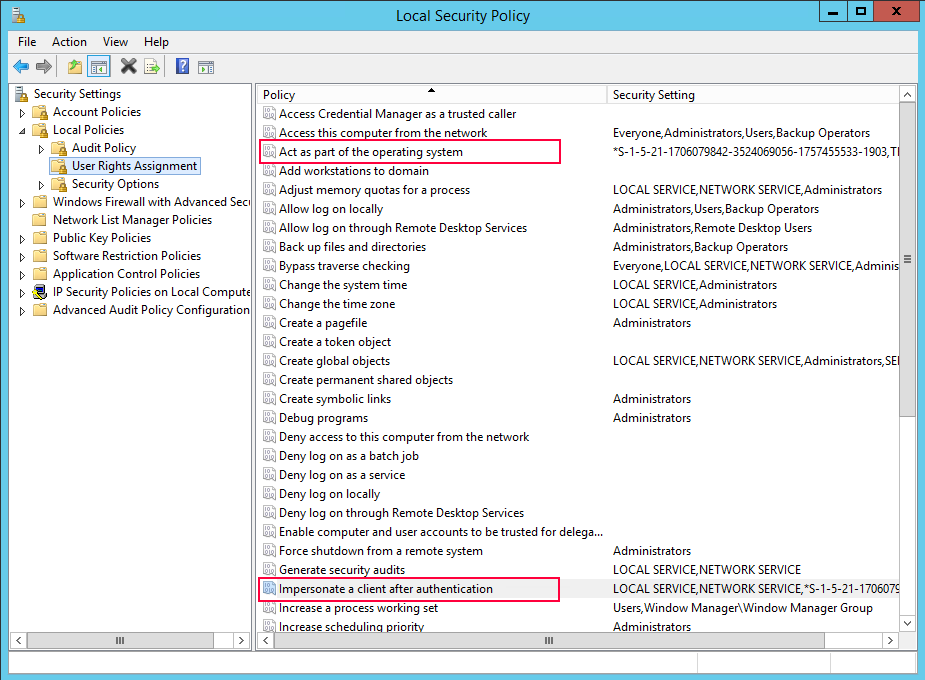
- Select [Local Policies > User Rights Assignment]
- Act as part of the operating system
- Impersonate a client after authentication
- Change the registry settings of the server machine:
| Field | Registry Entry |
|---|---|
| SubKey | HKEY_LOCAL_MACHINE\SOFTWARE\SAP\gsskrb5 |
| Entry | ForceIniCredOK |
| Type | REG_DWORD |
| Value | 1 |
SAP Source Settings #
Note: An existing SAP connection to a Single Application Server or Message Server is the prerequisite for using SSO with SNC.
- In the main menu of the Designer, navigate to [Server > Manage Sources]. The window “Source Details” opens.
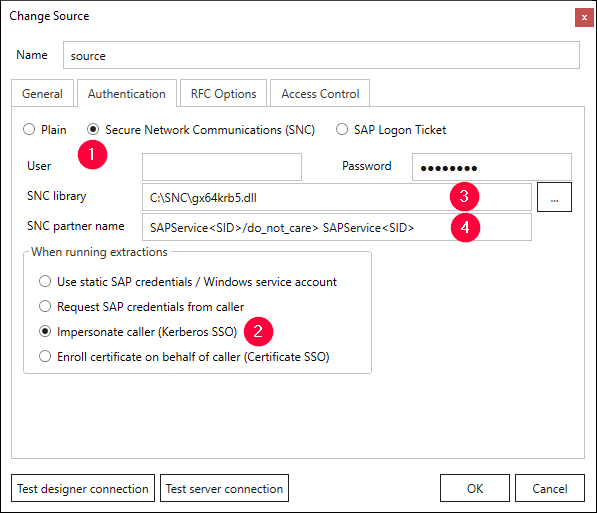
- Select an existing SAP source and click [Edit] (pencil symbol).
- Enable the SNC option (1) in the subsection Authentication.
- Enable the checkbox Impersonate authenticated caller (SSO) (2).
- Enter the complete path of the Kerberos library in the field SNC library
e.g.,
C:\SNC\gx64krb5.dll(3). - Enter the SPN of the SAP service account in the field Partner name. Use the following notation: p:[SPN]@[Domain-FQDN-Uppercase] (4).
- Click [Test Connection] to verify your connection settings.
- Click [OK] to confirm.
Note: The SAP Logon Pad SNC settings for partner name differ from the ones used in Xtract products. SAP Logon Pad uses the UPN of the SAP service accounts and Xtract products use the Service Principal Name (SPN). Use the following notation: p:[SAP Service Account]@[domain]. SPN’s are case sensitive in the SNC partner name.
SNC Activation in SAP #
In SAP, apply the Kerberos SNC settings as described in the SAP Help.